Federated authentication
Federated (or claims based) authentication, introduced in 10.2, provides your site with the ability to use a third party identity provider to authenticate users. The identity provider can be a fully independent system and is brokered by the Azure Access control system ACS). Alternatively you can enable your own active directory to be an identity provider also via ADFS2 (see the associated download on this page for details). Federated authentication is an option for both deployed and hosted systems.
In terms of configuration the login and logout are created using magic words :::federated-login:::
:::federated-logout::: on the relevant templates or pages. The site configuration takes place in site settings
The process is as follows:
- The user clicks 'login' link made using the above magic word.
- This redirects off to the Federated Login Server, where they choose a login method, e.g. live, active directory, yahoo etc
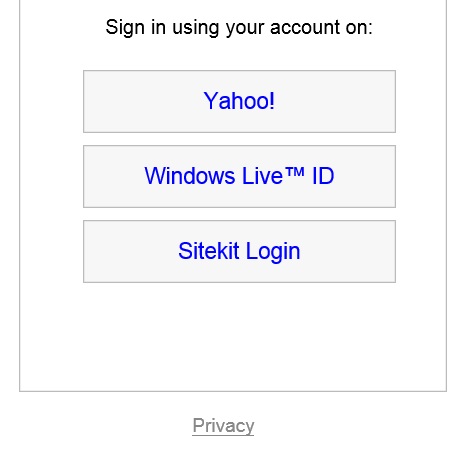
- They login using their chosen identity provider.
- The federation service sends them back to a special Sitekit page, passing some credentials.
- This pages creates the local Sitekit user, if necessary. It starts a visitor session for them, logs them in and then returns back to the original page in item 1
- Based on what master group the user is in, they now get permission to view the page/site.
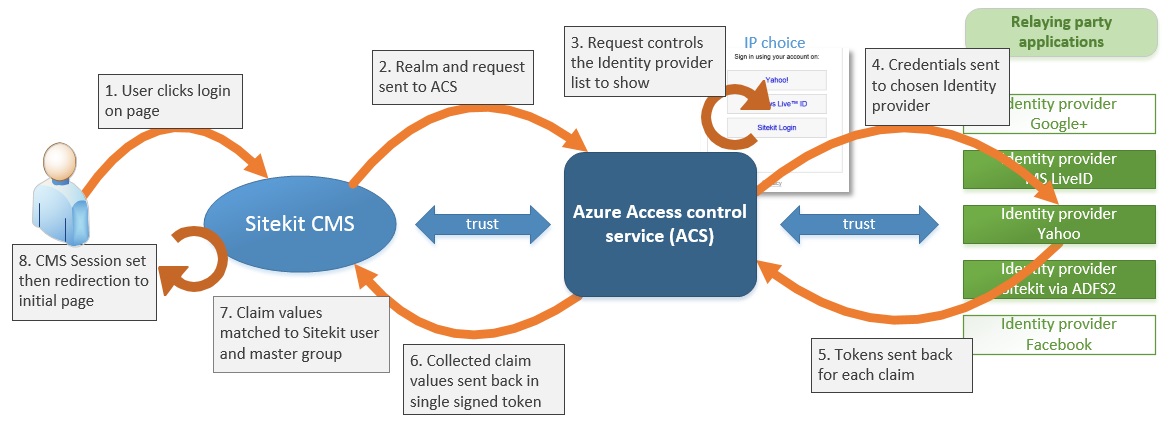
In detail the sequence from user, through CMS, ACS and identity providers and back to user is shown below
The following can be set up as an example with all the relevant settings in place in the site settings
<a href=":::federated-login:::">Federated Login</a><br/> <a href=":::federated-logout:::">Federated Logout</a><br/> <p> People ID = :::peopleid:::<br/> Username = :::username:::<br/> Fullname = :::fullname:::<br/> </p>
For MS liveID users, whilst the user is authenticated we get nothing back about the specific user, so they just default to 'Federated Anonymous'.
For AD Users, we get back full name, email, job, user groups. They are put into the master group that is specified in the Site Settings and as for WIA and web service based authentication they are also added to user groups that have names matching those in Active Directory.